Crucial Secure Access Services Edge Market Insights for the coming years reveal a fundamental shift in the very philosophy of enterprise security, a change that goes far beyond a simple technology refresh. The most profound insight is that SASE represents the architectural manifestation of a "Zero Trust" security model. The traditional, perimeter-based security model operated on a flawed principle of "trust but verify," where once a user was "inside" the corporate network (either physically or via a VPN), they were often granted broad access to a wide range of resources. The SASE model completely inverts this. It operates on a principle of "never trust, always verify." In a SASE architecture, no user or device is trusted by default, regardless of their location. Every single access request to an application is treated as a new, untrusted connection that must be explicitly and continuously verified based on the identity of the user, the health and posture of their device, and the context of the request. This granular, identity-centric approach to security, enabled by the ZTNA component of SASE, dramatically reduces the attack surface and is a far more effective model for the modern, distributed enterprise. The insight is that SASE is not just a new set of tools; it is a new and superior security philosophy made practical.
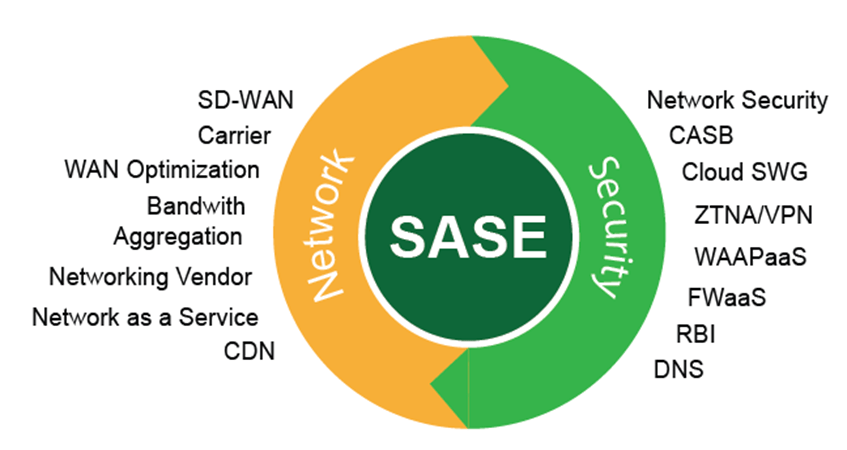
A second key insight is that the SASE purchasing decision is a unique one, as it represents a convergence of two traditionally separate organizational silos and budgets: the networking team (run by the CIO) and the security team (run by the CISO). In the past, these two teams often made their technology purchasing decisions independently. The networking team would choose the routers and the MPLS provider, and the security team would choose the firewalls and the web gateways. SASE forces these two worlds to come together. A successful SASE deployment requires a solution that can meet the needs of both stakeholders—the CIO's need for network performance, reliability, and cost-effectiveness, and the CISO's need for a robust, comprehensive, and compliant security posture. This has changed the competitive dynamics. The vendors who are most successful are those who can effectively articulate a value proposition that appeals to both personas. They must be able to have a credible conversation about both BGP routing and advanced threat prevention in the same meeting. The vendors who are still only talking to one side of the house are at a significant disadvantage.
A third critical insight is that SASE is rapidly evolving from being just a security and networking platform to being a Digital Employee Experience (DEX) platform. As companies compete in the "war for talent," providing a fast, seamless, and frustration-free digital experience for employees has become a major business priority. A slow, clunky, and unreliable security tool is a major source of employee dissatisfaction and productivity loss. The leading SASE vendors have recognized this and are now competing on their ability to deliver a superior user experience. They are investing heavily in building out their global PoP networks to minimize latency, and they are developing sophisticated monitoring tools that provide deep visibility into application performance from the end-user's perspective. The insight is that SASE is no longer just about blocking bad things from happening; it is about enabling good things to happen faster. It is being repositioned as a platform that not only secures the business but also makes its employees more productive and engaged. The Secure Access Services Edge Market size is projected to grow to USD 42.86 Billion by 2035, exhibiting a CAGR of 22.1% during the forecast period 2025-2035.
Top Trending Reports -